In this edition of WCTF blog we welcome guest blogger 0rsu who was a member of the second place team of the DEFCON WCTF challenge.
void main ()
{
I
rolled into Vegas this year much as I have the past four years: miserably hot
and already over the idea of dealing with hilljacks in douchetastic mall-chic
apparel. I’m among the fortunate of
those going to DEFCON in that I work for a company that I convince (con) into
paying my way out. So, I get here nice
and early on Wednesday, and I have plenty of time to get ready to pilfer my
weasely black guts out at DEFCON in style.
This
is a recollection of a relative newbie, and how with the help of a small team
of perfect strangers, we were able to capture second place in one of the most
prestigious wireless hacking contests. I
won’t go into too many of the intimate details of the competition, because I’m
sure those tricks will be used again.
But within I hope to give those sitting on the sidelines a little
insight on why you should definitely compete next year, and what to expect.
A
little about me, and how I got to this point.
I have been a general security engineer/analyst for a few years now,
after transitioning out of more than a decade-long, aggravating career in
general IT, where I put in my time educating the computer illiterate on where
to find the Start button, and the difference between a computer and a monitor. I don’t expect sympathy here. I know most people reading this have similar
tales, or are still neck deep in that hell.
At any rate, I have some experience in security, but it consists mostly
of building defensive systems. I like
the attack surface that wireless provides, since it tends to produce less of a
trail of breadcrumbs back to the attacker.
There’s just something ninja-like about pulling information literally
out of the air.
I
came to DEFCON with a nerd-on for SDR (software defined radio), and as it
turned out, spent almost zero time working or learning anything about it. This is mostly because the first talk I went
to was in the Wireless Village, where I decided on a whim to sit down and
compete in the wireless capture-the-flag.
In doing so, I flipped my usual script of roughly 90% of my time spent
in various talks. I still had a blast,
and learned quite a bit. Because I was
competing, I didn’t have the luxury of hashing out the finer points of
SDR. However I managed to open the door
to spending the coming year soaking in everything SDR by virtue of my drive to
win the wCTF next year.
The
Wireless Village at DEFCON, I should immediately point out, consists of every
RF-based discipline. Not just Wi-Fi. In the context of the wCTF, there is ample
time to learn and explore an unknown technology. That’s half the point in my opinion. Along with Wi-Fi, there are challenges
involving various SDR disciplines, Bluetooth, and this year even a crossover
into Wi-Fi-accessible SCADA/ICS systems.
To succeed in at least a few of the challenges from each group is to
have come to DEFCON and actually learned a new skill – one that you will
probably still remember once the hangover is gone.
The
other value in these exercises is the idea of nailing down a technique you might
know to some extent, but only ever used it in a limited way, and thus still
require a trip to Google to pull it off.
This was where I stood going in with regard to basic techniques like
using the Aircrack-NG suite. Sure, I’d
managed to perform a WEP crack before. But
pre-wCTF, even with a gun to my head I couldn’t have completed the steps
without a reference. After a weekend in
the challenge, I can run the main tasks of Aircrack-NG about as easily as
signing my name. (Full disclosure, my
signature looks like I’m trying to sign with my feet. While trying to stay afloat in a vat of KY
Jelly. While having a seizure.)
So, in
my four previous trips to DEFCON, I have managed to make almost zero meaningful
or long lasting connections with other con-goers. I tend to drift from talk to talk as a
wallflower. There are a few videos to be
found out there where I have spoken up in the Q&A, and in one or two cases
received applause for my remarks. But
even when someone has come up to me afterward, my anti-social tendencies render
me as Teflon as I scuttle off to my next talk, squirming away from the
friendliest of people. This all changed
in the span of one morning, as I sat down at a table of complete strangers and
got to work. I initially began the
challenge flying under my own banner.
But as I began to trade the occasional comment with the other three at
my table, something crazy happened - I started bonding with them. I made an arbitrary decision to grab some
lunch, and offered to grab food for anyone at my table. The guy and the girl sitting opposite me took
my offer, and suddenly and without fanfare, a winning team was born. That is literally all it takes. Offer to fetch some pizza, and you too can
manage to meet a few good hackers.
My
new team, who I will refer by their handles, consisted of rux616 and InvaderTAK,
apparently work with each other as CS interns.
This was their first time at DEFCON, and they were jumping in with both
feet, doing something it took me five years to break down and try. I envy their foresight in gaining more value
from the con than the handful of talks that would be freely available later
anyway. I would classify the three of us
as rookie material – especially at the start of the event. While we all have technical specialties, it
did not necessarily translate well into the contest. Personally, I spent a good three hours the
first day scratching my head trying to figure out why I couldn’t make it past
the first challenge. It was breaking WEP
for crying out loud! I thought I was
being fancy by pulling up Fern to automate the task and sat back, only to be
puzzled on why nothing happened. The
short version is: don’t just assume the wireless adapter you know and trust has
injection capabilities on a new OS build.
Run the stupid Airodump test, even if you think it’s a given. It was humbling to go half a day into the
contest with nothing to show for it. But
after a few speed bumps, I found my rhythm and began turning in
challenges. The other two on my team
faced similar troubles getting off the ground, but both managed to start
turning in good work.
It
is worth telling that capture the flag is an addictive game. To be honest, the thing that made me decide
to drop in to the challenge was the possibility of earning the nifty copper
challenge coins they give to those that place in the contest. Little did I know the prize haul in store
this year, including the coveted Black Badge – free DEFCON for life! After about 24 hours I was somewhat
regretting the decision to sit down. But
once you start earning points and seeing your name/team go up in the standings,
it’s hard to stop. My mild case of FOMO
was easily tempered by the thought of doing even mildly well in a contest I
thought was steeply beyond my expertise.
Without
detailing every challenge and every solution, I will just go through a few of my
thoughts about the contest. First, if
you have a laptop, you have everything you need to get started. The only other things I would recommend would
be a cheap SDR adapter, and maybe one or two extra USB Wi-Fi adapters (capable
of packet injection). All told, apart
from your laptop, you might have to invest $50 in your arsenal. My next insight is as I have mentioned above. Talk to people. Even if it’s not in your nature. The lone gunman hacker is a nifty persona to
emulate, but among tens of thousands of people that are, for the most part,
almost begging to include you in their social circle and teach you anything you
want to know, it’s worth following the advice you hear pretty much everywhere
at the con. These people are your people.
Trust them (just don’t send any valuable information over the hotel Wi-Fi). Buy them beer and marvel as the floodgates of
knowledge and experience wash over you.
The
folks that run the wCTF started their talk in the best way possible: with
absolutely nothing approaching reverence or propriety. These were a few ‘gentlemen’ that clearly
were here for the enjoyment of it, and like most people, were eager to pass on
knowledge. They were funny, they were delightfully
crude, they were instantly welcoming to all.
While they kept the competitors at an arm’s length for obvious reasons,
they were perpetually friendly. As soon
as they began speaking, I registered them in my mind as my kind of people. During the contest, they were happy to help demonstrate
the requisite techniques needed to pass the challenge, and they did so in a
positive and laid back manner.
The
challenges themselves are fun, and are given mysterious clues. The types of clues that have you smacking
your forehead once you figure them out.
Some challenges are ...more fun for spectators that the person
involved. I tender this GIF of me on the
business end of a dog training collar as what was probably a highlight for my
teammate with his finger on the keyboard that triggered the collar.
https://imgur.com/a/koceJ
I think
I might have wandered into the ICS village for a total of 5 minutes at a
previous con, but in this environment I was forced to put myself through a
crash course of all things related in order to pass the challenges. Is knowledge of ICS/SCADA something I will
use next week at work? I highly doubt
it. Will this information benefit me in
my career? It’s very possible. For those still trying to get their foot in
the InfoSec door, I can tell you that the more arrows you have in your quiver,
the better your chances will be. My
company doesn’t really do much with ICS, but that’s not to say my CTO will
decide tomorrow to roll out a new revenue channel I will suddenly be
responsible for securing. So in the end,
I was grateful to learn new skills.
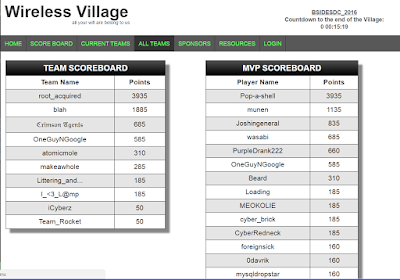
My
small team of neophytes managed to progress almost to the top of the
scoreboard. Indeed, I personally came
within ten points of the top individual score.
Above us was a large team of engineers from a major network/firewall
vendor, who’s collective experience far surpassed mine. So once it became obvious that they were the
Katie Ledecky of this particular race, I respected their knowledge and efforts
and congratulated them on their success.
At the same time, I am here to tell you that I will be spending a good part
of the coming year learning - sharpening my axe so that next year my team can
take down that particular marine-themed monster team and win the entire thing.
And
that may be the best part of my experience.
Learning begets learning. I come
to DEFCON generally, not as much to learn, but to be inspired to learn. This year I did both. And coming in second, especially now that
there is a black badge at stake, I
know there will be tougher competitors, and that we will be among them –
seasoned and ready for a bigger challenge.
I say bring it on. I have no
doubt that word will spread that the wCTF is an opportunity to score serious
hacker cred, as well as a ton of cool prizes and gear. Next year, my team and I will compete as
veterans. And while I know the
competition will be open and friendly as ever, I also know the gauntlet has
been dropped. Next year, it is on like
Donkey Kong.
}
We would like to sincerely thank Orsu and team, not just for this wonderful write-up, but also for exemplifing exactly what we are trying to accomplish. We run this game to provide a safe space to practice and test your skills, but above all we do it to share our passion with others. We do this in the hopes that we ignite a new love (or rekindle an old one) in our attendees and contestants. Many previous winners, near winners, and people who play have stories just like this. Please, come in, sit down, play, make friends, and join a welcoming group of your new friends.
-The Wireless Village and Wireless CTF Team